Curtis Collicutt
Outcome Oriented Technologist, Sales Engineer, and Cybersecurity Expert

About Curtis
Curtis is a technologist who works to make systems safer and easier to use. He adopts a socio-technical approach to complex challenges via human-centred solutions. Throughout his career, which has spanned work with university libraries, start-ups and enterprises, he has been a trusted advisor to customers and stakeholders. He is constantly learning and growing, and through organisations like TAICO, he helps others do the same.
Books
Technical books and resources for developers and security professionals.
The Safety Continuum
From Dry-Run to Digital Twins: A Guide to Building Safer Systems
Book One - Mechanics of Safety
First in a series about operating complex systems without burning out the people who run them. The book introduces a Safety Continuum, a framework for making day-to-day operations safer and more predictable.
Our industry has poured effort into uptime and availability but largely ignored the experience of the humans holding everything together at 3AM with brittle, dangerous tools. Safety is not the same thing as availability, and we have been treating it as an afterthought.
This volume (and the ones that follow) is about changing that. The tools and practices exist. Operators just need permission to use them.
95 pages ~20,000 words 8.5 x 11 PDF
The Stegalographer Guidebook
They said never write your own encryption. They didn't say anything about steganography.
This guidebook covers Stegalographer, the tool, and steganography more broadly.
Stegalographer adds watermarks and attribution markers to log files. If your logs already flow through a pipeline, Stegalographer slots into that pipeline and encodes information you can verify later, without disrupting anything visible.
Most people think of steganography as hiding messages in images, but the same idea works anywhere you have controllable variation. Distributed infrastructure already produces massive volumes of logs and metrics with natural variation baked in. That variation is a surface you can write on.
The security world has spent decades on encryption and availability. Steganography solves a different problem: provenance and attribution. Who produced this data? Has it been tampered with? These questions matter most in democratic and institutional systems, and they are the ones encryption alone cannot answer.
72 pages ~15,000 words 8.5 x 11 PDF
Software
Open source tools and commercial software for developers and operators.
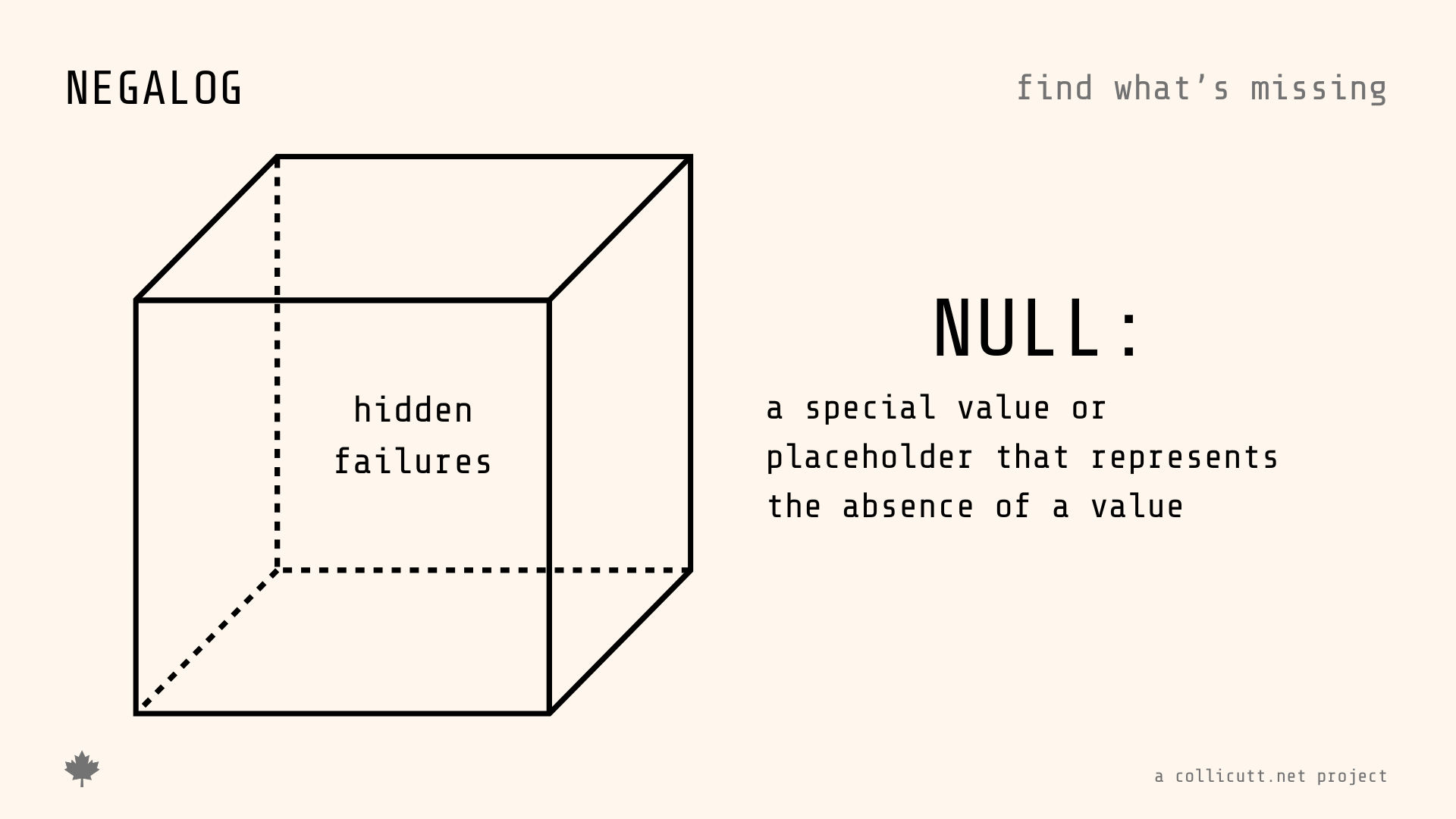
NegaLog
Find the logs that should exist but don't
Monday morning. You walk in to find the payment processing job stopped running Friday at 6pm. No errors. No alerts. It just...stopped. Three days of orders sitting unprocessed. $47,000 in delayed revenue. Angry customers. A manager asking "how did no one notice?"
The job didn't fail - it silently disappeared. Your monitoring watched for errors, but there were none. The absence of expected logs went undetected.
This is why NegaLog exists. Instead of watching for what went wrong, it watches for what should have happened but didn't.
Traditional log analysis tools search for patterns that exist. NegaLog inverts the paradigm: define what logs should exist, and it reports what's missing. Detect incomplete transactions, monitor scheduled jobs, and verify error handling - all by identifying the absence of expected log entries. Open source CLI tool written in Go with support for sequence detection, periodic monitoring, and conditional absence detection across multiple log files.
NegaLog supports commercial plugins for production use. See NegaLog Watch for continuous monitoring.
MCP Makefile Server
A Model Context Protocol server that provides makefile target inspection and execution capabilities for AI assistants.
Pure OSS - MIT License - PRs welcome, free to fork

raillock
A cybersecurity CLI tool and Python library for checksumming Model Context Protocol tools and securing your agents against prompt injection attacks.
Pure OSS - MIT License - PRs welcome, free to fork
Safeline
A Python framework for building safety-critical operations with arbitrary stage pipelines, audit trails, locking, and approval workflows.
Pure OSS - MIT License - PRs welcome, free to fork

rmrf
A safer version of `rm -rf`; designed for saving weekends
Pure OSS - MIT License - PRs welcome, free to fork

Go App Template Skeleton
A generic golang application skeleton providing a foundation for building API servers with web interfaces and command-line tools.
Pure OSS - MIT License - PRs welcome, free to fork

plothole
Test your AI-assisted code for missing implementations, TODOs, and other AI generated artifacts
Pure OSS - MIT License - PRs welcome, free to fork
Volunteer
Non-profit organizations and volunteer work I'm involved with.
Content
Content I create, like videos, blog posts, and more.
YouTube
This is where I publish videos about technology, cybersecurity, discuss my blog posts, and more.

Server As Code Dot Com
A techno-blog for our techno-times. This is where I write about specific applications of technology.

TIDAL SERIES
TIDAL SERIES is my newsletter where I tackle advanced ideas about computing, cybersecurity, artificial intelligence, financial markets, and more.
Social
Social and professional links.